BACHELOR OF COMPUTER APPLICATIONS
(BCA)
ASSIGNMENTS
Year, 2009
(6th Semester)
CS-74 CS-75
CS-74 CS-75
SCHOOL OF COMPUTER AND INFORMATION SCIENCES
INDIRA GANDHI NATIONAL OPEN UNIVERSITY
MAIDAN GARHI, NEW DELHI – 110 068
|
| |
|
|
CONTENTS:
| Assignment No. | Submission-Schedule | ||
For Jan-June Session | For july-Dec Session | |||
| CS-72 | BCA(6)-72/Assignment/09 | 15th April,2009 | 15th October,2009 | |
| CS-73 | BCA(6)-73/Assignment/09 | 15th April,2009 | 15th October,2009 | |
| CS-74 | BCA(6)-74/Assignment/09 | 15th April,2009 | 15th October,2009 | |
| CS-75 | BCA(6)-75/Assignment/09 | 15th April,2009 | 15th October,2009 |
__________________________________________________________
Course Code : CS 72
Course Title : C++ and Object Oriented Programming
Assignment Number : BCA (6)-72/Assignment/ 09
Maximum Marks : 25
Last Date of Submission : 30th April, 2009/30th October, 2009
There are eight questions in this Assignment. Answer all the questions. You may use illustrations and diagrams to enhance your explanations. Answer to each part of the question should be confined to about 300 words.
Q. 1 Explain four major advantages of Object Oriented Programming with the help of an
example each. (2 marks)
Q. 2 Explain the following terms in the context of object oriented programming. Also explain how these concepts are implemented in C++ by giving an example program for each.
(a) Single Inheritance
(b) Abstraction
(c) Encapsulation
(d) Function Overloading
(4 marks)
Q. 3 Explain the concept of late binding and dynamic binding with the help of at least two examples. Are these concepts related to polymorphism? Explain your answer.
(2 marks)
Q. 4 What is the need of UML? Explain the use of any two diagrams used in UML with the help of an example of each.
(2 marks)
Q. 5 Explain the usage of the following C++ operators with the help of an example program.
(a) sizeof operator
(b) bitwise AND operator
(c) ++ as post increment operator
(d) Dereferencing operator
(2 marks)
Q. 6 Write a function swap that exchanges the values of two variables using a third variable, by using the:
(a) Pointers
(b) & (address of) operator
Explain the two functions that you have written.
(2 marks)
Q. 7 Create a class hierarchy for the Worker and Supervisor using C++. The Worker class should include details like worker ID, Name, address of the worker, department ID and Supervisor ID. The classes should have necessary functions to input the required information and a polymorphic function to print the details of the workers or supervisors. For the worker’s this print function should output the worker ID, Name and Supervisor ID. Whereas for the supervisor’s this function should out put the Name and department ID of the supervisor. Please note that a supervisor is also a worker. Make and state suitable assumptions, if any.
(4 marks)
Q. 8 Write a template class “stack” in C++. The class should have functions for push, pop, stack full and stack empty. Use this template to create a stack of integer and a stack of character. Make suitable assumptions, if any.
(3 marks)
Q. 9 Create a class IntStr that stores a positive decimal integer as a string (the maximum number of decimal digits in the string can be assumed to be only 5 digits, so the maximum value that can be stored is 99999, whereas minimum value that can be stored is 00000.). The class should have a copy constructor, and an overloaded + operator. The overloaded + operator should perform the addition. On addition using this + operator, if the length of result exceeds 5 digit then the class should give the result as 00000. Write the necessary main() function to demonstrate the use of the class.
(4 marks)
__________________________________________________________
Course Code CS-73
Course Title : Theory of Computer Science
Assignment Number : BCA(6)-73/Assignment/2009
Maximum Marks : 25
Last date of Submission : 30th April, 2009/30th October, 2009
This assignment is having five questions. Answer all the questions.
Q. 1 Define the following concepts formally/mathematically, with one example for each:
a) Regular Language
b) Primitive Recursive Function
c) Turing Machine
d) Unsolvable Problem
e) Turing-Decidable Problem
f) Mealy Automata
g) Universal Turing Machine
h) Deterministic Finite Automata
i)Context-Free Grammar
j) Godel Number
(5 marks)
Q. 2 Construct a DFA (Deterministic Finite Automata) accepting the following
Set:
w has an even number of a’s and odd number of b’s }
(5 marks)
Q. 3 Construct Turing Machine for the following languages:
(i) {anbncn : n > 1}
(ii) {wwR : w is any string of 0’s and 1’s} (5 marks)
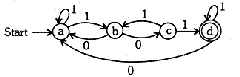
Q. 4 Find the minimum state finite automaton equivalent to the following
transition diagram :
Q. 5 Design the Push Down Automata (PDA) which accepts the language:
__________________________________________________________
Course Code : CS-74
Course Title : Introduction to Internet Programming
Assignment Number : BCA(6)-74/Assignment/09
Maximum Number : 100 (weightage = 25)
Last Date of Submission : 30th April, 2009/30th October, 2009
This assignment is having six questions. Answer all the questions.
Q. 1 Answer the following questions through examples:
(i) What are the benefits of inheritance in Java programming? (6 marks)
(ii) What are the applications of super and this keyword? (2 marks)
(iii) What is the use of the final modifier? (2 marks)
Q. 2 (i) What is the input and output to a Java compiler?. (2 marks)
(ii) What is the relationship between Java and HTML? (2 marks)
(iii) What is the import statement for? (2 marks)
(iv) What are the differences between application and applets? How do you
run an application and an applet? (9 marks)
Q. 3 (i) Describe the JAVA throughable class hierarchy and types of exceptions.
(10 marks)
(ii) What is the purpose of claiming exceptions? (3 marks)
(iii) What is the keyword throw and throws used for? (2 marks)
Q. 4 Design a menu-driven interactive programme to find out capital cities of all the states of India using switch statement. (20 marks)
Q. 5 Admission to a professional course is subject to the following condition:
a) Marks in mathematics > = 60 (20 marks)
b) Marks in Physics > = 50
c) Marks in Chemistry > = 40
d) Total in all three subjects > = 200
Or
Total in mathematics and Physics > = 150
Given the marks in the three subjects, write a programme to process the applications to list the eligible candidate.
Q. 6 Write a programme to perform binary operations on integer argument. The arguments and operators should be accepted using command line parameters.
(20 marks)
__________________________________________________________
Course Code : CS-75
Course Title : Intranet Administration
Assignment Number : BCA (6)-75/Assignment/ 09
Maximum Marks : 25
Last Date of Submission : 30th April, 2009/30th October, 2009
There are five questions in this assignment. Answer all the questions. You may use illustrations and diagrams to enhance your explanations.
Q. 1 Define the term “Intranet”. (3 marks)
Q. 2 Define the term “Extranet”. (3 marks)
Q. 3 Explain the differences between Internet and Intranet. (3 marks)
Q. 4 How can it be ensured that the transactions that take place across Intranet are secure? Explain with an example. (10 marks)
Q. 5 What is Internet Protocol Version 6.0? Explain any two features of it?
(6 marks)
__________________________________________________________

How to create READ MORE in Blogger platform!
Today i create a new blog on Blogger platform. I write some posts and when i want to put ”Read more” on a post i can find it! I search on the Internet, i found something
but with few explications. Now i want to write this tutorial with some printscreens! Let’s start!
[1] Login to your blogger account and go to Settings

[2] Now click on Template

[3] Now click on Edit HTML

[4] Before editing click on the check box of Expand Widget Templates,
to see the complete structure of your page
![]()
[5] Search this: ( Find with your Browser: Edit -> Find )
<b:if cond=’data:blog.pageType != “item”‘><br />

[6] Now you need to write this code: <a expr:href=’data:post.url’>Read more!</a>
[7] You finished, now when you create a post and if you want ot put “Read More”,
write this:
<span class=”fullpost”></span>
Example:
About hamid-info.blogspot.com<span class=”fullpost”>Read more</span>

| You love games but you don’t understand the mumbo jumbo? Here are some of the terms most commonly used by gamers around the world and their meanings. |
Playing Games on your PC doesn’t make you a gamer. To truly become a gamer, you must understand the spirit of gaming. The first step in the process of becoming a gamer is to understand the gamin terms. Given below are a few of the commonly used gaming terms with their meanings:
|
A. SUB GENRE 1. FPS : FPS stands for First Person Shooter. The term FPS is used in action games played from a first person’s perspective, i.e. you play through the eyes of the character you control. Eg : Half life is a FPS game. 2. TPS : TPS stands for Third Person Shooter. The term TPS is used in games where the character which is controlled is viewed from a distance, i.e. the camera seems to be behind the characters head. Eg. : Max Payne is a TPS game. 3. RTS : RTS stands for Real Time Strategy. The term RTS is used in strategy games which are not turn based, i.e. the game continues playing irrespective of whether you make your move or not. Eg. : Age of Empire is a RTS game. 4. SIM : Sim is short for simulation. The term sim or simulation is used for games that simulate reality. Eg. : Flight simulator is a sim. 5. MMORPG OR MMO : MMORPG stands for Massive Multiplayer Online Role Play Games. The term MMO is used for online games that have many players playing simultaneously. The term RPG (Role Play Games) is used when players assume the role of a fictional character in a fantasy are combined with role play, MMORPG is born. |
| |
|
B. IN GAME TERMS 1. GAMEPLAY : Gameplay basically refers to anything you do in the game. The term gameplay is used to define the overall experience of the game with respect to the gamer. Eg. : running, Shooting, Jumping etc all constitutes to gameplay. 2. HUD : HUD stands for Heads Up Display. It is usually the area on screen that contains the basic information about the character. Eg. : Health, ammo, map etc are displayed on the HUD. 3. AI : AL stands for Artificial Intelligence. AI is basically the measure of the intelligence of characters in the game that are not under the user’s control. Eg. : If you are shooting at bad guys in the game and they don’t duck for convers it shows poor AI. 4. BOT : BOT is short for robot. The term bot is used to refer to computer controlled characters in the game. Eg. : During online play, if the teams are unbalanced, bots are used to fill the gap. 5. RESPAWN : RESPAWNING is the recreation of a game character after its death or destruction. Eg. In counter strike, usually you cannot respawn until the end of the round where as in games such as Unreal you can respwan as soon as you die. |
|
C. MISCELLANEWOUS TERMS 1. RL : RL stands for Real Life. This term is usually used by gamers to differentiate between the gaming chat and real life char. Eg. I am an emperor here, but a student in RL. 2. CRACK : A crack is a small file or code developed by a cracker. A crack is used in pirated games to bypass its security. 3. PATCHES : Patches are small or medium size files which could be developed by the developer or cracker. Patches are minor updates used to improve a programme. Eg. If a game has very high loading time, patches could be released to rectify this. 4. BUGS : A bug is an error in the game or malfunction in the gaming code. Eg.: Hands becoming transparent, gun going inside walls, getting stuck at corners etc while playing a game are all bugs. 5. EXPANSION PACK : Expansion packs are an addition to existing games like extra level, new characters etc with the essence of the game till being the same. Expansion packs may or may not be dependent of the original. 6. PLATFORM : The different consoles on which a game can be played is called a platform. Eg. : The commonly used platforms are PC, PS3, and Xbox. 7. LAG : This condition occurs usually during online play and is caused due to congested network or a slow systems. When your movements are slower than the others you are said to be lagging. 8. DEVELOPERS AND PUBLISHERS : A Develper is a company or an individual who has created the game from scratch and Publisher is the company or companies which sell the game to the public. |

The local area network (LAN) is home to sheer bandwidth and countless client server applications. Different companies have radically different networks; some have a single PC and others have hundreds of locations and thousands of computers. This page is intended to explain the basic principles and components frequently found on the LAN. The internal network is usually built with the highest bandwidth available. It is then connected to a tiny internet connection which is almost always a bottle neck for internet traffic. Most businesses of any size have at least one server to provide extra computing features to the business. The internet is explicitly distrusted and generally the network has protection from the internet built in. The LAN is something that businesses have complete control over. Network devices are much simpler than servers and PCs. It is common (and best practice) to duplicate significant portions of the Network to allow for failure without having a noticeable impact on the network. A LAN is the local cabling and set of network devices at an individual location building or campus but the internal network can easily include many LANs connected to form a WAN.
The internal network, and therefore the LAN, exists to link all of the PCs, laptops, servers, printers, and anything else that might be useful for a computer to talk to. Most LANs have a cable running from every computer to a wall jack. The wall jack is connected to a very similar type of cable that runs to a patch panel in a wiring closet. A patch panel is simply a bank of cable ports that allows all of the cables coming from each wall jack to be connected to the LAN if desired. Any active wall jack must have the corresponding port in the patch panel connected to a switch in the wiring closet. A wiring closet is a centralized room where these cables end. It is common for there to be many wiring closets in a building. The standard is that these wiring closets not actually be used for anything else besides LAN equipment, although this rarely happens in practice. If there are many switches in a wiring closet, they are connected to one or two switches within in the same closet. These serve to connect all of the switches there as well as some of the cable runs entering the room. The switches in a wiring closets are connected to a centralized switch or switch pair in a main wiring closet. The centralized switch or switch pair serves to connect the entire LAN together. These distribution switches connect to the router(s) that the location may have to further connect the switches to the internet or the enterprise WAN thus extending the LAN.
The internet is full of hackers which means that the traffic that comes from the internet is usually distrusted. On most local area networks there are more things that communicate or are set up to communicate than are used and fewer that are really needed. However everything that is on a computer that communicates on the LAN is a potential vulnerability for a hacker to exploit. For this reason most networks use a firewall which simply restricts what can communicate (IP address) to what is on the other side of a firewall and what type of communications (port number) can pass through it. Generally this means that only the things frequently used are allowed to pass through it. The idea is that anything that is not a business need is not allowed through which greatly reduces what a hacker can attack. In reality it does leave many options open for attack, although it is certainly a much smaller set of options than what would be available without it. Because the servers that communicate directly with the internet are considered the highest risk these are frequently placed in what’s called a demilitarized zone (DMZ). This simply means that the traffic to and from these servers and the normal internal network is restricted by additional firewalls. Some DMZ’s have additional firewalls inside them to further protect the LAN from any internal threat.
There is usually a firewall between the internet and the internal network (LANs); that is the firewall is placed between the internet border router and the adjacent core switch to protect the LAN. A firewall is simply a device that restricts communication and helps improve security much like a guard post does. Firewalls are also commonly used to segregate off anything else that is considered a higher risk. If there are any servers that accept connections from the internet there is frequently a demilitarized zone (DMZ). With DMZ’s a firewall is placed both between the servers and the internet and between the servers and the internal network (both LAN and WAN). This reduces the probability and impact of a server being hacked. (A hacked server on the network is a serious risk to the rest of the network and common practice is to remove it from the network regardless of it’s purpose.) There are frequently additional firewalls within a DMZ to further reduce the security risk within the DMZ. It is also common to have an intrusion detection system (IDS) at various points of the WAN, especially in the DMZ and internet connection where there is the greatest chance that an attack will happen. Unlike a firewall an IDS is not necessarily intended to stop malicious activity but rather to simply detect it, log it, and possibly notify the appropriate persons.
Many people enjoy being able to use a wireless connection to connect to the LAN rather than having cables connected to their laptop. This means that there are (depending on the size of the building) many antennas installed throughout the building. These antennas are called access points. Because the reception area provided by the access points is relatively small there are many access points connecting to each wiring closet. It is worth noting that because each access point potentially connects many computers it is much cheaper to install wireless than it is to install physical cabling to each computer. However there are many drawbacks of wireless. It is possible for someone who would not normally be allowed to both connect to the LAN to connect and to intercept the connection. Both are considered security risks. The first allows a hacker, potentially off company property, to connect to sensitive systems only accessible to employees on the LAN. The latter allows a hacker to read sensitive information being transmitted such as passwords, e-mails, etc. There are steps that can be taken to reduce this risk such as encrypting the wireless signal and placing all of the wireless traffic behind a firewall on the outside of the regular LAN. Wireless communication is somewhat slower than the physically cabled counterparts as well. For these two reasons, most businesses do not connect most of their computers to a wireless connection with exceptions for some laptop users. This may not be allowed for non-employee access and is treated as a security risk. It is common to find wireless access points on a LAN.
The LAN connects most of the computers and devices together with switches. A switch is basically a large bank of network cards. The switch is what connects all of the cables. A patch panel looks similar to a switch from the front but merely provides a convenient and neat way to end the cables collected in a wiring closet. A patch panel connects nothing and is just a large multi-port panel where a switch is an electronic device that connects these electronically to the LAN. Switches switch small chunks of traffic at lightning speed between whichever cables the traffic needs to go through to reach the destination. Many of these allow administrators to login from a portion of the LAN to administer the connections and advanced settings. The number of cable connections that a single one can support varies. These are a more advanced technology than a hub which has been replaced by switches in all modern LAN’s. Many of these devices in a modern network are layer 3 switches which means that they are also capable of acting as a router. If there are enough computers to require many switches, the switches connect to each other and are arranged with one or two switches connecting all of the other switches. Most larger networks contain many switches.
A router is the device that connects different smaller networks (LAN’s) together to form a WAN or MAN. The purpose of a router is to determine the next route a packet of data should take to get to the destination most efficiently. This simply means picking a device it is connected to and forwarding the packet to that device which is closer to the destination. There are usually only one or two routers in most offices. However larger networks have multiple routers at central locations such as the headquarters, data centers, and carrier’s facilities. Routers are usually only connected to only other switches and routers. Routers are generally more advanced than switches. These devices contain knowledge of the entire network where switches normally only contain knowledge of the individual LAN they service. If there is more than one office (thus multiple LANs) then there is normally a virtual circuit used to connect the locations together for which the company spends additional money. For example frame relay and asynchronous transmission mode (ATM) connections both create a virtual connection between the LANs. This means that only network traffic between the two locations can pass through and security precautions normally needed for internet connections are not necessary. This is true even though there may be a great deal of distance between the locations. Virtual private networking (VPN) can also be used for the same effect which is implemented very differently. Because this uses encryption to form the virtual circuit, it is often used to connect corporate laptops on the internet to the internal network.
If there is a shared resource, such as a website, that is used by many people there are sometimes many servers that provide the service. A load balancer is used to determine and regulate exactly how each individual server provides which portion of the load within the LAN. This provides both greater capacity (multiple servers are sharing the load rather than just one) and reliability (theoretically) as long as there is one server left the service is still available. In practice a load balancer may improve reliability but it can never be guaranteed to always detect a failure and rebalance the load without using the failed server. Similar means of balancing loads can be done other ways. For example a DNS server can simply rotate the IP address given for a DNS entry. This is how Google rotates load between different servers at different data centers. It is rare for a load balancer to balance the load to dissimilar devices or devices not on the same LAN segment.
It is common for a network to contain a proxy. A proxy is used to restrict web access, filter viruses, and move some of the load on the internet connection to the LAN. This is simply a server that caches web pages and retrieves those that are not in the cache from the internet. This allows any requests for the same web page to be loaded from the cache on the LAN rather than the internet connection reducing the load on the LAN connection. For example if two people both go to Google’s home page early in the morning the second one does not have to be loaded from the internet. This saves bandwidth. This is also sometimes used to restrict the sites that employees can go to as well as record where they go. There are companies that compile lists of websites by category intended for use as a type of parental control over the employees. For example a business can display a web page saying access denied whenever an employee tries to go to a porn site from work. Some businesses have also reported tremendous success with distributing a list of the employees who visit porn sites the most at work throughout the company. Similar things can be done with game sites where employees may waste time, racist, bigot, or malicious websites. Some people object to proxies citing privacy or censorship concerns.
Businesses’ networks almost always have at least one server on the LAN. Very large companies may have hundreds of servers. It is considered best practice to have at least two redundant network cables connected to the servers that also connect to different switches for a reliable LAN connection. This sometimes requires software installed and configured on the server to ensure that if one LAN connection fails it starts to use the other one. It is possible to have more than one LAN connection and load balance these but this requires special configuration on the switch as well as the server. If the network connection is load balanced it provides better performance due to the double sized network connectivity. Severs also are the first to receive the latest cabling and network cards. Because servers are used by many people it is often attractive to upgrade the network connections long before the rest of the network. These are often also much easier to upgrade because they are usually in the same room as the switch so the manual labor and cable length used is minimal.
Most businesses have directory services in place. This is normally considered an application level service rather than part of the LAN. This simply means that there is one or more servers on the network which are tasked with authenticating passwords and possibly other related tasks such as storing user settings. Whenever there is a need for user authentication, such as logging intro a computer or accessing a network file share, a authentication request is sent to the directory services server. This prevents someone who may have been able to gain unauthorized physical access to an enterprise PC from logging into any computer on the LAN. Of course if the intruder happens to obtain the username and password of an employee this will do little good. This is also used for internal employees to use a single password. The password is valid for shared resources such as network file shares and applications in a controllable and restrictive manner. Some examples are active directory and NIS.
There are a lot of components to the internal business network. Local area networks (LAN) are usually fairly modern and very fast and make up a great portion of the internal network. However these are almost always connected to an internet connection that is significantly slower. For this reason there are many things that can be done on a LAN or WAN that are not financially feasible on the internet. This page kept it very simple, but if you look around you will find more information on this site about local area networks and networking in general.

In general terms, LAN (Local Area Network) refers to a group of computers interconnected into a network so that they are able to communicate, exchange information and share resources (e.g. printers, application programs, database etc). In other words, the same computer resources can be used by multiple users in the network, regardless of the physical location of the resources.
Each computer in a LAN can effectively send and receive any information addressed to it. This information is in the form of data 'packets'. The standards followed to regularize the transmission of packets, are called LAN standards. There are many LAN standards as Ethernet, Token Ring , FDDI etc. Usually LAN standards differ due to their media access technology and the physical transmission medium . Some popular technologies and standards are being covered in this article.
Media Access Control methods
There are different types of Media Access Control methods in a LAN, the prominent ones are mentioned below :
![]() Ethernet - Ethernet is a 10Mbps LAN that uses the Carrier Sense Multiple Access with Collision Detection (CSMA/CD) protocol to control access network. When an endstation (network device) transmits data, every endstation on the LAN receives it. Each endstation checks the data packet to see whether the destination address matches its own address. If the addresses match, the endstation accepts and processes the packet. If they do not match, it disregards the packet. If two endstations transmit data simultaneously, a collision occurs and the result is a composite, garbled message. All endstations on the network, including the transmitting endstations, detect the collision and ignore the message. Each endstation that wants to transmit waits a random amount of time and then attempts to transmit again. This method is usually used for traditional Ethernet LAN.
Ethernet - Ethernet is a 10Mbps LAN that uses the Carrier Sense Multiple Access with Collision Detection (CSMA/CD) protocol to control access network. When an endstation (network device) transmits data, every endstation on the LAN receives it. Each endstation checks the data packet to see whether the destination address matches its own address. If the addresses match, the endstation accepts and processes the packet. If they do not match, it disregards the packet. If two endstations transmit data simultaneously, a collision occurs and the result is a composite, garbled message. All endstations on the network, including the transmitting endstations, detect the collision and ignore the message. Each endstation that wants to transmit waits a random amount of time and then attempts to transmit again. This method is usually used for traditional Ethernet LAN.
![]() Token Ring - This is a 4-Mbps or 16-Mbps token-passing method, operating in a ring topology. Devices on a Token Ring network get access to the media through token passing. Token and data pass to each station on the ring. The devices pass the token around the ring until one of the computer who wants to transmit data , takes the token and replaces it with a frame. Each device passes the frame to the next device, until the frame reaches its destination. As the frame passes to the intended recipient, the recipient sets certain bits in the frame to indicate that it received the frame. The original sender of the frame strips the frame data off the ring and issues a new token.
Token Ring - This is a 4-Mbps or 16-Mbps token-passing method, operating in a ring topology. Devices on a Token Ring network get access to the media through token passing. Token and data pass to each station on the ring. The devices pass the token around the ring until one of the computer who wants to transmit data , takes the token and replaces it with a frame. Each device passes the frame to the next device, until the frame reaches its destination. As the frame passes to the intended recipient, the recipient sets certain bits in the frame to indicate that it received the frame. The original sender of the frame strips the frame data off the ring and issues a new token.
![]() Fast Ethernet - This is an extension of 10Mbps Ethernet standard and supports speed upto 100Mbps. The access method used is CSMA/CD .For physical connections Star wiring topology is used. Fast Ethernet is becoming very popular as an upgradation from 10Mbps Ethernet LAN to Fast Ethernet LAN is quite easy.
Fast Ethernet - This is an extension of 10Mbps Ethernet standard and supports speed upto 100Mbps. The access method used is CSMA/CD .For physical connections Star wiring topology is used. Fast Ethernet is becoming very popular as an upgradation from 10Mbps Ethernet LAN to Fast Ethernet LAN is quite easy.
![]() FDDI (Fiber Distributed Data Interface) - FDDI provides data speed at 100Mbps which is faster than Token Ring and Ethernet LANs . FDDI comprise two independent, counter-rotating rings : a primary ring and a secondary ring. Data flows in opposite directions on the rings. The counter-rotating ring architecture prevents data loss in the event of a link failure, a node failure, or the failure of both the primary and secondary links between any two nodes. This technology is usually implemented for a backbone network.
FDDI (Fiber Distributed Data Interface) - FDDI provides data speed at 100Mbps which is faster than Token Ring and Ethernet LANs . FDDI comprise two independent, counter-rotating rings : a primary ring and a secondary ring. Data flows in opposite directions on the rings. The counter-rotating ring architecture prevents data loss in the event of a link failure, a node failure, or the failure of both the primary and secondary links between any two nodes. This technology is usually implemented for a backbone network.
Topologies The various ways in which cables are arranged constitute the topologies in a LAN. Some of the Ethernet Topologies are described here :
|
LAN Components
| Basic LAN components . There are essentially five basic components of a LAN
|
| Network Communication devices A LAN comprises of different communication devices across the network such as the following :
|
| Physical Transmission Media Cables constitute the Physical Transmission Medium in a LAN and could be of the following types. Cables
|
| Asynchronous Transfer Mode (ATM) In recent years, with the boom in information technology leading to new GUI based applications, more emphasis is being given to improving backbone and inter LAN performance. This has lead to a new concept of connecting the backbone through ATM switches. ATM ( asynchronous transfer mode) is the switching technology where data is sent in forms of fixed length cells instead of packets of various lengths. The speed of , in case of the ATM switches, is comparatively much faster than the traditional Ethernet switch, as the network overhead is less for ATMs. |
| Internet Access over LAN There are various methods of connecting a LAN to the Internet Gateway, which are explained as below :
A common way of accessing Internet over LAN is the Dial-Up approach. In this method, a remote user gets to Internet as follows - Initially the remote user¹s PC is linked to the local gateway through an existing dialup line using modems, once the user has reached the local gateway, further routing up to Internet is taken care of, by the local gateway itself. The routing procedures are transparent to the end user. Leased line facility provides reliable, high speed services starting as low as 2.4kbps and ranging as high as 45 Mbps (T3 service). A leased line connection is an affordable way to link two or more sites for a fixed monthly charge. Leased Lines can be either fiber optic or copper lines High capacity leased line service is an excellent way to provide data, voice and video links between sites. Leased line service provides a consistent amount of bandwidth for all your communication needs. Integrated Services digital Network (ISDN) is a digital telephone system. ISDN involves the digitization of telephone network so that voice, data, graphics, text, music, video and other source material can be provided to end users from a single end-user terminal over existing telephone wiring. ISDN BRI (Basic Rate ISDN) delivers two 64 kbps channels called B channels and one at 16kbps (D channel). ISDN offers speed at 64 Kbps and 128 Kbps and is an alternative for those with a need for greater Bandwidth than dial service.For utilizing the ISDN service, the User needs to have an ISDN Terminal Adapter and an ISDN Card on the system. VSAT technology has emerged as a very useful, everyday application of modern telecommunications. VSAT stands for 'Very Small Aperture Terminal' and refers to 'receive/transmit' terminals installed at dispersed sites connecting to a central hub via satellite using small diameter antenna dishes (0.6 to 3.8 meter). VSAT technology represents a cost effective solution for users seeking an independent communications network connecting a large number of geographically dispersed sites. VSAT networks offer value-added satellite-based services capable of supporting the Internet, data, voice/fax etc. over LAN. Generally, these systems operate in the Ku-band and C-band frequencies. The Internet Access over cable modem is a very new and fast emerging technology. A "Cable Modem" is a device that allows high speed data access via a cable TV (CATV) network. A cable modem will typically have two connections, one to the cable wall outlet and the other to the PC. This will enable the typical array of Internet services at speeds of 100 to 1000 times as fast as the telephone modem. The speed of cable modems range from 500 Kbps to 10 Mbps. |

A Guide to Ethernet Components and Terminology
The power of an Ethernet LAN (Local Area Network) is tremendous when applied to a factory floor or other industrial application. However, to take full advantage of its features, it requires more than simple wire connections from one device to another. Following are descriptions and explanations of some of the infrastructure devices that can make your Ethernet LAN come alive.

Unmanaged Ethernet switches are a plug and play installation. Switches increase the number of nodes and the length of the LAN. They are designed to divide the network into separate collision domains. This reduces overall traffic on a LAN, improving communication speed and reducing errors.
Switches route communication to the desired end device instead of broadcasting the communication to everyone connected to the LAN. This is accomplished by the switch’s ability to set up a table of device addresses connected to each leg of the switch. With this information the switch knows where to send each Ethernet packet once it is received.
Managed Ethernet Switches allow advanced control of your LAN. They usually include software to configure your network and diagnostic ports to monitor LAN traffic. If communications fail, most managed switches will alert the manager via e-mail or by closing a relay to trigger an audible signal or flash a light. Another feature available on managed switches is QoS (Quality of Service) programming which prioritizes messages ensuring important data receives the highest priority on the LAN segment.
Ethernet Hubs are a simple way to increase the number of nodes, extend network distances while introducing the smallest amount of latency. Hubs don’t examine the Ethernet packets for destination information so they deliver
the packets even more quickly than a switch. All messages received by the hub are sent out on all legs to all the connected devices. Installation is a plug and play operation.
Media Converters change Ethernet twisted pair copper wires into fiber optic signals. Fiber optic is often preferable because it is impervious to interference that can disrupt the signals being carried by copper. Because fiber can extend the distance of a network up to 2 km in each segment, media converters can also increase the range of a network.
10BASE-T - 10 Mbps Ethernet communications over Category 3 or better cable.
100BASE-TX - 100 Mbps Fast Ethernet communications over Category 5 or better cable.
10BASE-FL - 10 Mbps Ethernet transmitted over fiber optic cable.
100BASE-FX - 100 Mbps Fast Ethernet transmitted over fiber optic cable.
Auto-negotiation - A protocol defined in the Ethernet standard that allows devices at either end of a link segment to advertise and negotiate modes of operation such as link speed (10 or 100 Mbps), half or full-duplex operation and full-duplex flow control.
MDI - Medium Dependent Interface. The name for the connector used to make a physical and electrical connection between a transceiver and a media segment. For example, the RJ45 style connector is the MDI for 10BASE-T and 100BASE-TX.
MDI-X - An MDI port on a hub or media converter with an internal crossover function. A “straight-through” cable can be used to connect a station to this port since the signal crossover is performed inside the port.
Quality of Service (QoS) - Some switches support QoS (per 802.1p and 802.1Q standards) wherein tagged messages can be assigned one of eight levels of priority. QoS can be important where time-critical applications can be affected by data delays.
VLAN - Virtual Local Area Network. A LAN that maps stations on a basis other than location — such as by department, user type or application. Managing traffic, workstations and bandwidth can be easier with a VLAN.
This improves network efficiency.
Structured Cabling — Nothing in Ethernet is left to chance. A set of cabling standards for design, installation, performance and testing provides a “structure” for Ethernet. (Refer to EIA/TIA 568 and ISO11801)

For Each Set
Total Marks: 20
Duration: 1 Hrs
Term End Practical, July 2008
BCS-061P (Set 1)
1) Run the following command & write its use. [5]
a. mail
b. cat
2) Write & run a program in c-language for a simple data transfer between a client & server machine using TCP Protocol. [15]
BCS-061P (Set 2)
1) Run the following command & write its use. [5]
a. ping
b. who
2) Write & run a program in c-language for implanting swap function, which exchange two socket addresses. [15]
CS-68P (Set 1)
1) How can you check the MAC address of your machine? Show it & writer all the steps. [5]
2) Examine the Ethernet in your Study centre. [15]
a) What new network components (transceivers, switch, router etc) did you find? Write detailed specifications of each.
b) What is the length of cable used?
CS-68P (Set 2)
1) How can you assign IP address to your machine? Show it & writer all the steps. [5]
2) We have a wire up to 200 meter of type UTP Cat5. We have to make a connection of one computer with another computer located at 200 meter. There are two additional switches also available for this purpose. Show how both computers will be connected. [15]

In SQL, there are essentially basically two ways to INSERT data into a table: One is to insert it one row at a time, the other is to insert multiple rows at a time. Let's first look at how we may INSERT data one row at a time:
The syntax for inserting data into a table one row at a time is as follows:
INSERT INTO "table_name" ("column1", "column2", ...)
VALUES ("value1", "value2", ...)
Assuming that we have a table that has the following structure,
Table Store_Information
| Column Name | Data Type |
| store_name | char(50) |
| Sales | float |
| Date | datetime |
and now we wish to insert one additional row into the table representing the sales data for Los Angeles on January 10, 1999. On that day, this store had $900 in sales. We will hence use the following SQL script:
INSERT INTO Store_Information (store_name, Sales, Date)
VALUES ('Los Angeles', 900, 'Jan-10-1999')
The second type of INSERT INTO allows us to insert multiple rows into a table. Unlike the previous example, where we insert a single row by specifying its values for all columns, we now use a SELECT statement to specify the data that we want to insert into the table. If you are thinking whether this means that you are using information from another table, you are correct. The syntax is as follows:
INSERT INTO "table1" ("column1", "column2", ...)
SELECT "column3", "column4", ...
FROM "table2"
Note that this is the simplest form. The entire statement can easily contain WHERE, GROUP BY, and HAVING clauses, as well as table joins and aliases.
So for example, if we wish to have a table, Store_Information, that collects the sales information for year 1998, and you already know that the source data resides in the Sales_Information table, we'll type in:
INSERT INTO Store_Information (store_name, Sales, Date)
SELECT store_name, Sales, Date
FROM Sales_Information
WHERE Year(Date) = 1998
Here I have used the SQL Server syntax to extract the year information out of a date. Other relational databases will have different syntax. For example, in Oracle, you will use to_char(date,'yyyy')=1998.

Tables are the basic structure where data is stored in the database. Given that in most cases, there is no way for the database vendor to know ahead of time what your data storage needs are, chances are that you will need to create tables in the database yourself. Many database tools allow you to create tables without writing SQL, but given that tables are the container of all the data, it is important to include the CREATE TABLE syntax in this tutorial.
Before we dive into the SQL syntax for CREATE TABLE, it is a good idea to understand what goes into a table. Tables are divided into rows and columns. Each row represents one piece of data, and each column can be thought of as representing a component of that piece of data. So, for example, if we have a table for recording customer information, then the columns may include information such as First Name, Last Name, Address, City, Country, Birth Date, and so on. As a result, when we specify a table, we include the column headers and the data types for that particular column.
So what are data types? Typically, data comes in a variety of forms. It could be an integer (such as 1), a real number (such as 0.55), a string (such as 'sql'), a date/time expression (such as '2000-JAN-25 03:22:22'), or even in binary format. When we specify a table, we need to specify the data type associated with each column (i.e., we will specify that 'First Name' is of type char(50) - meaning it is a string with 50 characters). One thing to note is that different relational databases allow for different data types, so it is wise to consult with a database-specific reference first.
The SQL syntax for CREATE TABLE is
CREATE TABLE "table_name"
("column 1" "data_type_for_column_1",
"column 2" "data_type_for_column_2",
... )
So, if we are to create the customer table specified as above, we would type in
CREATE TABLE customer
(First_Name char(50),
Last_Name char(50),
Address char(50),
City char(50),
Country char(25),
Birth_Date date)
Sometimes, we want to provide a default value for each column. A default value is used when you do not specify a column's value when inserting data into the table. To specify a default value, add "Default [value]" after the data type declaration. In the above example, if we want to default column "Address" to "Unknown" and City to "Mumbai", we would type in
CREATE TABLE customer
(First_Name char(50),
Last_Name char(50),
Address char(50) default 'Unknown',
City char(50) default 'Mumbai',
Country char(25),
Birth_Date date)
You can also limit the type of information a table / a column can hold. This is done through the CONSTRAINT keyword

A primary key is used to uniquely identify each row in a table. It can either be part of the actual record itself , or it can be an artificial field (one that has nothing to do with the actual record). A primary key can consist of one or more fields on a table. When multiple fields are used as a primary key, they are called a composite key.
Primary keys can be specified either when the table is created (using CREAT TABLE) or by changing the existing table structure (using ALTER TABLE).
Below are examples for specifying a primary key when creating a table:
MySQL:
CREATE TABLE Customer
(SID integer,
Last_Name varchar(30),
First_Name varchar(30),
PRIMARY KEY (SID));
Oracle:
CREATE TABLE Customer
(SID integer PRIMARY KEY,
Last_Name varchar(30),
First_Name varchar(30));
SQL Server:
CREATE TABLE Customer
(SID integer PRIMARY KEY,
Last_Name varchar(30),
First_Name varchar(30));
Below are examples for specifying a primary key by altering a table:
MySQL:
ALTER TABLE Customer ADD PRIMARY KEY (SID);
Oracle:
ALTER TABLE Customer ADD PRIMARY KEY (SID);
SQL Server:
ALTER TABLE Customer ADD PRIMARY KEY (SID);
Note: Before using the ALTER TABLE command to add a primary key, you'll need to make sure that the field is defined as 'NOT NULL' -- in other words, NULL cannot be an accepted value for that field.

BCA From IGNOU
The BCA provides an understanding and skills related to the use of computer and its application. Its design is based on the BDP programme of the IGNOU, with a special focus on computer application and possibly of moving on to an MCA after completing the BCA.
The minimum duration of the course is 3 years ad the maximum duration is 6 years. The facilities for counselling and practical second and third year will, however, not automatically be extended after first year of study. Practical sessions in subsequent years is at the discretion of the University and subject to payment for the same. During practical 2 students have to share one computer. In the first year total no of practical sessions is 40 (10 sessions in semester - 1 and 30 sessions in 2nd semester ). In 2nd year total number of practical session is 40 and in 3rd year total number of practical counselling sessions is 60. Each practical counselling session is equal to 3 hrs.
The BCA comprises of the following courses year-wise.
First Year
1st Semester & 2nd Semester
CS-610 : Foundation course in English for Computing
CS-612 : P.C. Software application Skills
FHS : Foundation Course in Humanities & Social Science
CS-60 : Foundation Course in Mathematics in Computing
CS-611 : Computer Fundamentals
CS-62 : C Programming & Data Structure
Second Year
2nd Semester & 3rd Semester
FST : Foundation Course in Science & Technology
CS-06 : Introduction to DBMS
CS-63 : Introduction to System Software
CS-64 : Introduction to Computer Organisation
CS-05 : Elements of System Analysis and Design
CS-65 : Window Programming
CS-66 : Multimedia
CS-67 : A RDBMS Lab
Third Year
5th Semester & 6th Semester
CS-68 : Computer Network
CS-72 : C++ and Object Oriented Programming
CS-69 : TCP/IP Programming
CS-73 : Theory of Computer Science
CS-70 : Introduction to Software Engineering
CS-74 : Introduction to Internet Programming (JAVA, ACTIVEX)
CS-71 : Computer Oriented Numerical Techniques
CS-75 : Intranet Administration
CS-76 : Project
After passing BCA 3rd year a student can join from MCA 2nd year

SELECT Syntax - Get Information from a table in database
SELECT ColumnName1,ColumnName2, ColumnName3 FROM TableName
SELECT DISTINCT ColumnName FROM TableName
SELECT COUNT (ColumnName) FROM TableName
SELECT ColumnName FROM TableName WHERE ColumnName = value
SELECT ColumnName FROM TableName WHERE ColumnName1 = value AND ColumnName2 = value
SELECT ColumnName FROM TableName WHERE ColumnName1 = value OR ColumnName2 = value
SELECT ColumnName FROM TableName WHERE ColumnName IN (Value1,Value2)
SELECT ColumnName FROM TableName WHERE ColumnName BETWEEN (Value1 AND Value2)
SELECT ColumnName FROM TableName WHERE ColumnName Like '%Value1%'
SELECT ColumnName FROM TableName ORDER BY ColumnName
SELECT ColumnName1 , SUM(ColumnName2 ) FROM TableName GROUP BY ColumnName1 HAVING (Arithematic Condition)
UPDATE Syntax
UPDATE TableName SET ColumnName = Value WHERE {Condition}
UPDATE TableName SET ColumnName = Value WHERE ColumnName = value
DELETE Syntax
DELETE TableName WHERE {Condition}
DELETE TableName WHERE ColumnName = value

Transaction Control
A TRANSACTION is a unit of work. A TRANSACTION may be a single action or it may be a series of actions. For example, if you add 5 records and all 5 records must be added before saving, that is a single transaction. If you add 5 records and you save between each, those are 5 discrete transactions.
NOTE: Whether or not the 5 transactions must be saved as one transaction or as multiple transactions is based on the business rules for an application. In general, the database does not care.
TRANSACTION CONTROL refers to the commands that allow you to save, or not, any data that you may have manipulated. Technically, transaction control has its own language, separate from DML called the Transaction Control Language or TCL. However, in most conversations, TCL is usually encompassed in DML. Regardless, TCL is important to understand before you start using DML.
Begin Transaction/End Transaction
The keywords “BEGIN TRANSACTION” and “END TRANSACTION” are part of the ANSI SQL standard. Unfortunately, not all vendors have implemented these keywords the same way. For some, the keywords are optional, other required. For some, END TRANSACTION is implicitly called by COMMIT or ROLLBACK and you will get an error by using this keyword. Others require an END TRANSACTION and will commit your data when called.
To make it a little more difficult, at least one database treats your DML and DDL commands differently depending on whether or not you call BEGIN TRANSACTION. For this database, if you do not explicitly begin the transaction, each successful DML command is auto-saved and any errors are rolled back. If you do explicitly begin the transaction, by calling BEGIN TRANSACTION, all commands are treated as a single transaction and are committed or rolled back together.
The easiest way to see if your database requires these commands is to check the documentation for your chosen database.
The important thing to remember about these keywords is that they really don't do anything to your data. They don't add data or change data. In some databases, using the END TRANSACTION will save any changes you have already made.
Synonyms for BEGIN TRANSACTION are BEGIN, BEGIN WORK and START TRANSACTION.
Rollback
ROLLBACK is arguably the most important command that you will learn. I call it, fondly, the “oops” command. With the ROLLBACK command you can undo any kind of DML. In many databases, you can even undo Data Definition Language (DDL) commands.
ROLLBACK will rollback all changes back to the beginning of a transaction. In some systems, that means back to the last BEGIN TRANSACTION, where as in other databases that means back to the last COMMIT or ROLLBACK.
In Oracle, DDL cannot be undone via ROLLBACK. DML can. You are not required to begin a transaction in Oracle and a ROLLBACK will rollback to the last COMMIT or ROLLBACK before it.
The syntax for a ROLLBACK is very simple:
ROLLBACK;
Many vendors like to extend the database with proprietary syntax extensions on the standard. Oracle, for example, adds the FORCE keyword to handle special situations with distributed transactions. One extension to rollback, albeit part of the standard, is rollback to savepoint. Not all databases support SAVEPOINT.
Savepoint
A savepointallows a developer or user to maintain multiple rollbackpoints in a SQLscript or procedure. You can use them interactively but that is less useful as it can quickly get confusing.
Savepoints allow nested rollbacks. You can execute a DML command, i.e. insert a record, issue a savepoint, insert another record and then rollback just the second insert. Without savepoints, a rollback would roll back both inserts.
Savepoint work by giving a name to a savepoint.
INSERT INTO taba(column1) VALUES (123);
SAVEPOINT first_savepoint;
INSERT INTO tabb(column2) VALUES (456);
To rollback all changes, we would use:
ROLLBACK;
To rollback just the second insert, we roll back to the named savepoint:
ROLLBACK TO first_savepoint;
It is possible for the script or session to have multiple savepoints.
INSERT INTO taba(column1) VALUES (123);
SAVEPOINT first_savepoint;
INSERT INTO tabb(column2) VALUES (456);
SAVEPOINT another_save;
INSERT INTO taba(column2) VALUES (456);
SAVEPOINT oogabooga;
INSERT INTO tabd(column3) VALUES (789);
We could roll back to any one of these:
ROLLBACK TO oogabooga;
ROLLBACK TO another_save;
Executing these two rollback commands would leave the first two inserts intact but would undo inserts 3 and 4.
Had we issued:
ROLLBACK TO first_savepoint;
None of the other savepoints would remain. Rolling back to a higher level savepoint invalidates the lower level savepoints. As a matter of a fact, if we executed:
ROLLBACK TO first_savepoint;
ROLLBACK TO oogabooga;
We would get an error in most databases.
Commit
The second most important command you can learn is the COMMIT command. Commit tells the database to save any additions, changes or deletions that you may have made. The basic syntax is very simple:
COMMIT;
In some databases, you may need to say:
COMMIT WORK:
In some databases, COMMIT WORK and COMMIT TRANSACTION are synonyms for COMMIT. As mentioned above, in some databases, END TRANSACTION is also a synonym for COMMIT.
Some extensions that you may see for the COMMIT keyword allow you to COMMIT your work but let you continue processing before the change is written to disk (NOWAIT) or to force a commit on distributed transactions (FORCE).
It's always important to review your vendor documentation for specific extensions to the SQL standard as some of these extensions are extremely valuable. For example, Oracle's NOWAIT extension can dramatically improve performance in certain situations where there is an extremely high transaction rate and during batch loads.
______________________________________
Source : http://databasewisdom.com/sql_toc_chapter2.shtml